The new year inspired us and brought new vibes to our office. Our tech ninjas are developing several new badass features. Besides the new features, we are also improving our existing modules as well. Last week, the SenseLog module became enriched with 4 new rules and another rule has been updated. Here is a list of them:
1. Apache Magento Downloader (Rule ID: 80_1_021)
2. Apache WP Login Deprecated Firefox User Agents (Rule ID: 80_1_022)
3. Plesk Login Fail (Rule ID: 8443_1_001)
4. LFD Blocked (Rule ID: lfd_1_001)
+1 Updated rule: Apache WP XML-RPC Suspicious User Agent (Rule ID: 80_0_018)
Let’s go through them one by one:
1. Apache Magento Downloader
We always keep an eye on our servers, that’s how we discovered a lot of attempts like this:
POST /downloader//downloader/index.php HTTP/1.1" 404 15605 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:62.0) Gecko/20100101 Firefox/62.0
This request came from a botnet, which is searching for the Magento Connect Manager, which is used for installing programs. It can be a security hole as well, that’s why the botnet is scanning the /downloader.
We received such requests from more than 5,000 IP addresses so we greylisted these malicious IPs with the following command:
cat access*.log | grep POST |grep 404| grep downloader | /opt/bitninja/modules/Cli/scripts/greylist_apache_log.php
Of course, it is needed permanently, so we created a new SenseLog rule (80_1_021) to block this botnet on your servers too.
2. Apache WP Login Deprecated Firefox User Agents
We have already talked about why it’s important to secure your WordPress sites’ login page
. However, a ton of users are still using the default wp-login, and that’s why botnets love to make an attempt against it. Just like this log shows:
[11/Feb/2019:10:13:56 +0100] "POST /wp-login.php HTTP/1.1" 200 3849 "http://#####.eu/wp-login.php" "Mozilla/5.0 (Windows NT 6.0; rv:34.0) Gecko/20100101 Firefox/34.0"
Sending a POST request to /wp-login.php from this User Agent is quite suspicious, so we created a new SenseLog rule, so in cases like this, the IP will be automatically added to the BitNinja greylist.
3. Plesk Login Fail
The Plesk panel is getting more popular nowadays (that’s why BitNinja is added to their Extensions
), so it’s no surprise that it became the botnet’s new playground. Besides the old-fashioned WordPress brute force attacks, the Plesk brute force attack appeared too.
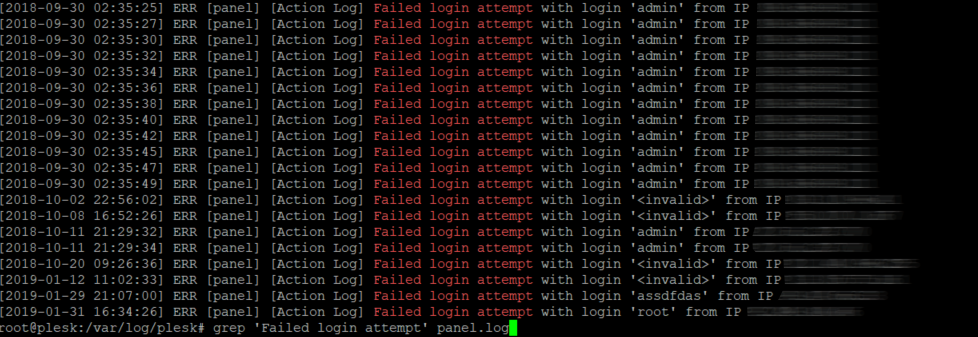
We listed all the IPs with the following command and got hundreds of IP addresses which failed to log in.
/var/log/plesk# grep 'Failed login attempt' panel.log | cut -d' ' -f15 |sort | uniq -c
Thanks to this new SenseLog, attacks like this will be blocked, so Pleskians can lean back. 😉
4. LFD by Blocked
Some BitNinja users are still using LFD besides BitNinja, so this rule was created especially for them. When LFD is blocking an IP, it remains blocked for 3600 seconds and a log like this will appear in /var/log/lfd.log:
Nov 21 19:07:46 force1 lfd[12949]: (sshd) Failed SSH login from ###.###.###.### (US/United States/domain.com): 5 in the last 3600 secs - Blocked in csf for 3600 secs [LF_TRIGGER]
The lfd_1_001 SenseLog is watching the „Blocked in CSF” messages. Currently, this rule is in „Log only” mode, which means that an incident will be generated, but the IP won’t be blocked yet. We need to analyze the results of this rule deeper, but after we make sure that it won’t cause false positives, we’ll change it to „Challenge and greylist IP” mode.
+1 Updated rule: Apache WP XML-RPC Suspicious User Agent
When someone is sending a request to the XML-RPC, the question always arises: Is it an XML-RPC attack
now? Not always, but when it’s coming from a suspicious agent, it makes the answer obvious. That’s what happened when we found logs like this on our servers:
[11/Feb/2019:10:07:03 +0100] "POST /xmlrpc.php HTTP/1.1" 200 411 "-" "Mozilla/5.0 (X11; Linux i686; rv:2.0.1) Gecko/20100101 Firefox/4.0.1"
[11/Feb/2019:10:07:06 +0100] "POST /xmlrpc.php HTTP/1.1" 200 411 "-" "Mozilla/5.0 (X11; Linux i686; rv:2.0.1) Gecko/20100101 Firefox/4.0.1"
This User Agent in these logs is a really old one (the latest version of the Firefox is 65) and valid users don’t send POST requests to XML-RPC from it, only IoT botnets can make it.
An existing SenseLog rule (80_0_018) was updated with this piece of information. If an IP is sending POST /xmlrpc.php from Mozilla/5.0 (X11; Linux i686; rv:2.0.1) Gecko/20100101 Firefox/4.0.1 then the IP will be greylisted automatically.
Stay safe with BitNinja!
As you can see, we are continuously upgrading our software and provide protection against a wide range of attacks in every phase of the attack cycle. With BitNinja Pro, your servers are in the best hands, so if you are not part of our fantastic Ninja Community yet, do not waste your time anymore. Join us
to kick the hackers’ and bots’ butt together.
