There is a huge demand for buying botnets on the Dark Web, so it’s not a surprise that new kinds of botnets appear from time to time in order to meet the needs of the cybergangs. Of course, there are some old but constantly attacking botnets, like the most popular Mirai botnet
or the Hello Peppa botnet
which was discovered and named by us. However, we’d like to show you a new botnet, that we haven’t talked about yet. This is the Hexa botnet.
Discovery of the Hexa botnet
Back in March, we introduced our new security module, the Defense Robot
. It was a pleasure to us that we could release the first automatic malware root cause analysis tool of the market. But the results brought by this module was even more fascinating.
Actually, this module is what helped us to discover the Hexa botnet. We saw that 70% of the infections originated from one type of backdoor. And guess what... this was the Hexa botnet’s backdoor!
You don’t have to worry about that we „kept in secret” this botnet for months because right after this botnet caught our attention, we implemented a behavior-based protection on to our Malware Detection and WAF modules in order to keep our ninja friends’ servers safe against this botnet.
Since the discovery, we detected ~150,000 Hexa botnet attack attempts on our customers’ servers in the past 3 months and most of the C&C request came from the US:
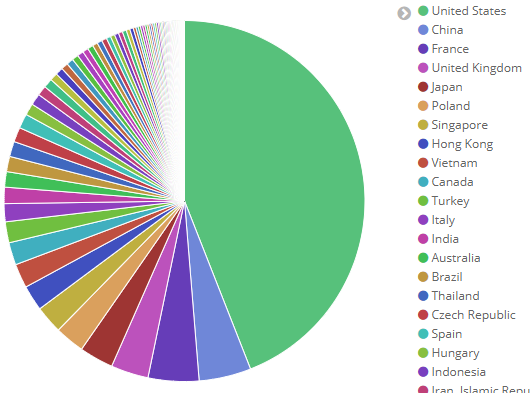
How does a Hexa botnet attack look like?
Once you saw a Hexa botnet log, it’s very easy to spot this botnet. The backdoor’s file name is always 8 random characters and the content is especially obfuscated. Hackers use hex coding in this case, so because of the hexadecimal characters, you can see random numbers and letters in the log, but no recurring expression. That’s how the hackers are trying to trick the security vendors, as the usual method to filtering an exact string command (which refers to PHP codes) is impossible with the hexa botnet. But it hasn’t tricked us! We implemented a behavior-based protection, which I show you a bit later. Before that, let’s take a look at a Hexa botnet log:
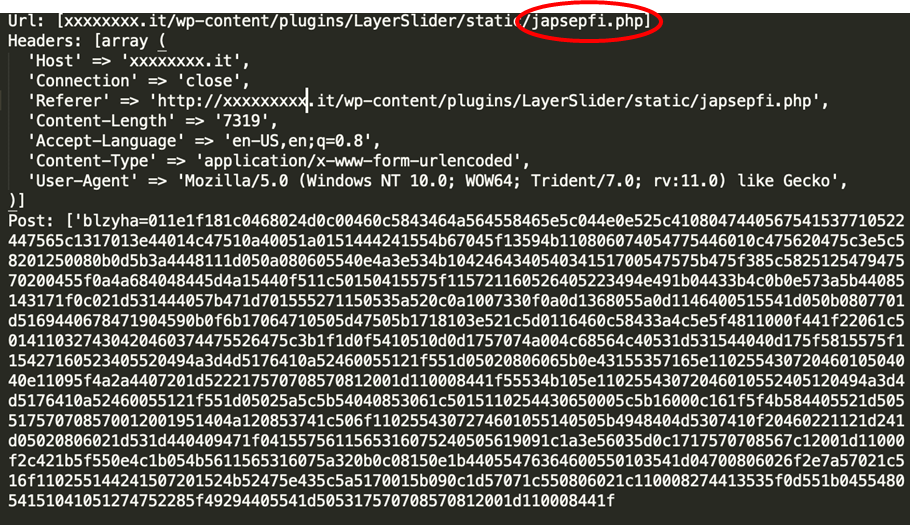
Hexa botnet is specialized in attacking WordPress sites. Even if you only host a single WordPress site on your server, you can still become the target of Hexa botnet. Hackers don’t care about the size of your business size. The only thing that hackers care about is quantity. Essentially, this means that every WP site owner is in danger.
“Just because WordPress has such a wide distribution, it is important to make sure this environment is sufficiently protected. With BitNinja, this security is given.” - Joachim Ruisz (ruisz.com)
We have already helped Joachim to keep their WP sites safe, and now, we’d like to help you too.
Protection against the Hexa botnet
BitNinja provides you a powerful and convenient way to stay safe against Hexa botnet (and of course against the other types of cyber attacks). Let’s see how we fight against Hexa botnet:
1. IP Reputation: We have identified a huge number of infected servers which have already attempted to attack any of the thousands of BitNinja protected servers worldwide. But... they failed to get through our protective shield. Our database not only contains these zombie machines but we are already blocking many C&C servers too.
2. Malware Detection: When there is a hexa botnet backdoor upload attempt, our Malware Detection will identify the infected file and place the backdoor into quarantine.
BitNinja will not only quarantine the backdoor but it will also block the attacker IP by the Defense Robot module.
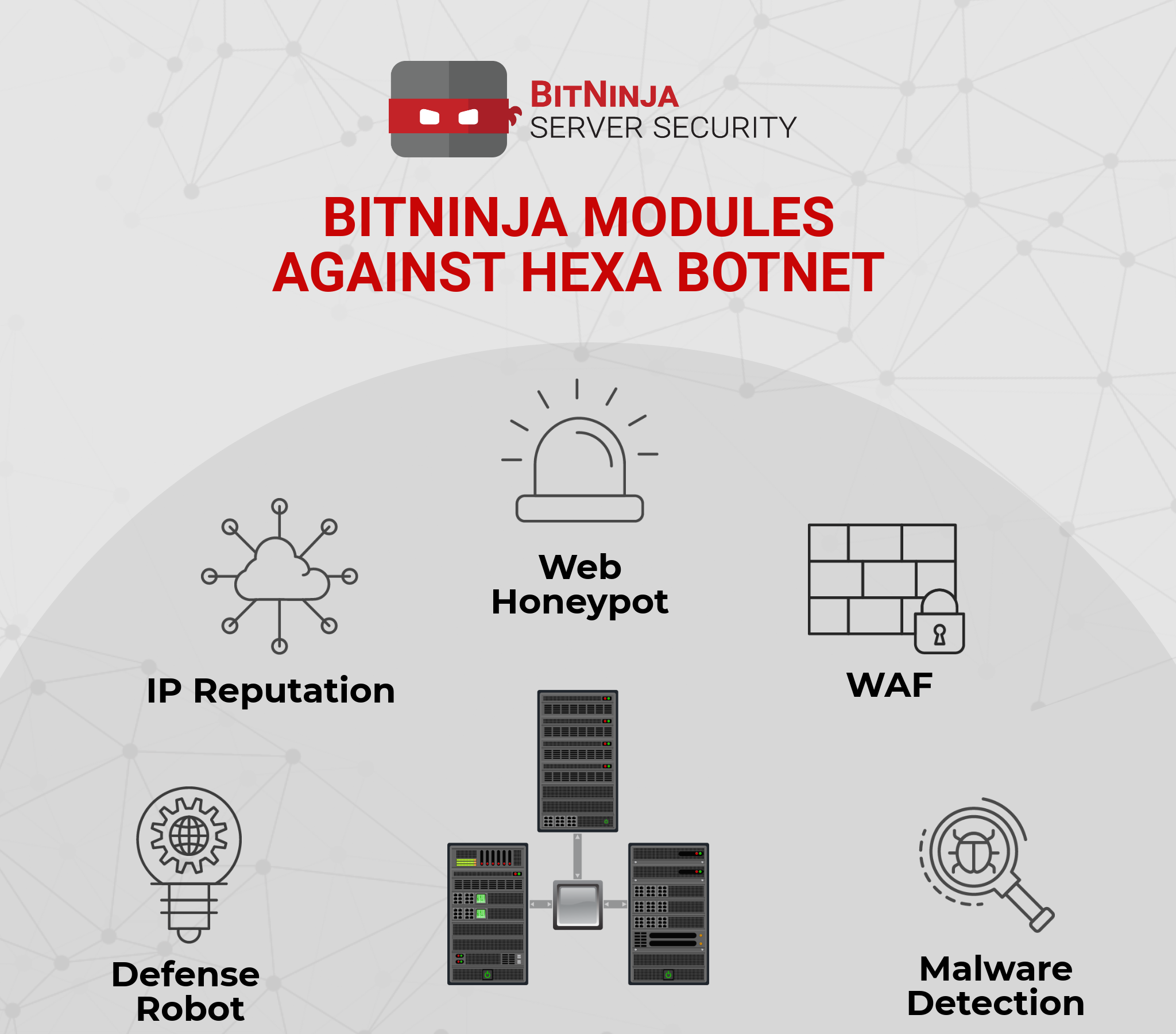
3. Defense Robot: Defense Robot helped us discovering this flood of attacks, and it is still helping to keep the BitNinja protected servers safe against this botnet. When an attacker is trying to upload the backdoor, this module will find and block the malicious IP, meaning that it won’t be able to attack you or our other BitNinja clients.
4. Web Honeypot: BitNinja will not only block the backdoor uploader, but it can even detect C&C server IPs as well. There is a technique called “honeypotify”, which means that BitNinja will create a web honeypot from the infected file/backdoor. This way, the C&C server will believe that the backdoor is existing on your server and it will try to send requests to it. But as the backdoor is only a honeypot, the request will be blocked immediately and the IP won’t be able to connect your servers.
5. BitNinja WAF: This module will protect your servers in two ways:
- Usually, attackers exploit WordPress vulnerabilities to upload a backdoor on your server. In most cases, hackers can’t even exploit the vulnerability, as BitNinja patches the most critical WordPress vulnerabilities.
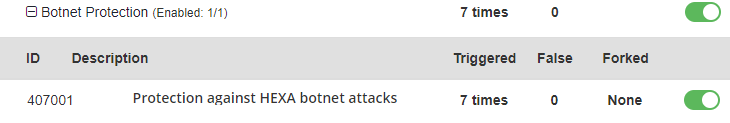
- If a backdoor was uploaded to your server before installing BitNinja (and you haven’t run a manual malware scan to discover existing infections
), the 407001 BitNinja WAF rule will stop the C&C server’s command from running.
Botnets on the rise
Not the Hexa botnet is the one which is spreading quickly nowadays. There are different kind of motivates behind the hackers’ actions, which results in an increasing number and type of cyber attacks. If you’d like to learn more about the botnet ecosystem, check out our new e-book. You can find even more details about the Hexa botnet too.
Download free e-book now
BitNinja will help you to avoid your servers being part of a botnet, so feel free to contact us if you have any questions or need assistance. 🙂
You can see the results with your own eyes too. Haven’t tried BitNinja yet? Now, you can get a 7-day free trial.



