We always keep our eyes on the logs, data, and charts. We always see abnormalities and unusual behaviours, we have found botnets before, but our recent catch is one of the biggest. These cases are really hard to handle due to the huge number of affected IPs.
On the evening of 14th June, we have seen something strange, the average incident number increased by nearly 200%. But that was just the beginning, later on, there was a period when we received over five times more incidents. After 24 hours, we had four times more data than on an average day. We have captured a new botnet, which attacked the BitNinja protected servers. Thanks to our databases we can present this whole case to you. 🙂
How did these attacks look like from security perspective?
First of all, the attacker was searching for the xml-rpc.php files of the domains, so it looked for a potential vulnerability that can be attacked by a single request. Which potential vulnerability can be contained in xml-rpc requests? You can read more about it in our previous article.
If the request was successful, and the scan found the .php file, the attack continued with a login request, with the most common username and password pairs, that can be found in every dictionary attacks. This pattern shows up in all of the cases, a file scan and only one login attempt. It raises an interesting question. Why did they use the vulnerable plugin of a vulnerable site only once?
The user agent of the requests was spoofed like most of the xml-rpc attacks and it was a FireFox/40.1 Agent. How do you know whether a user agent is fake? Here, you can find a list of the most common user agents.
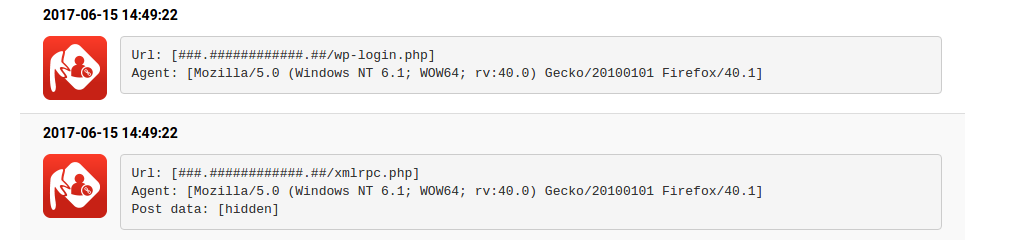 The scannings were in alphabetical order by the domain names, and we had one attack attempt for a server. So, a single server has never been attacked twice by the same IP. We don’t know the exact reason for it, maybe the attacker tried to avoid the blacklisting of his/her botnet.
The scannings were in alphabetical order by the domain names, and we had one attack attempt for a server. So, a single server has never been attacked twice by the same IP. We don’t know the exact reason for it, maybe the attacker tried to avoid the blacklisting of his/her botnet.
However, we have observed a really important detail. Nearly all of the attacker IPs are part of dynamic IP ranges of mobile broadband services from different countries.
What does it mean? Is it a new security threat?
We believe the attack is coming from an IoT botnet, that hasn’t attacked until 14th of June. As you know, most of the IoT botnets are built by infected IP cameras, DVC systems, routers and other smart devices. Do you remember when a refrigerator and it’s other 100000 partners SPAMmed the whole word? So, we can never mention it often enough, take care of your smart devices and keep them updated. 🙂
Some BitNinja statistics
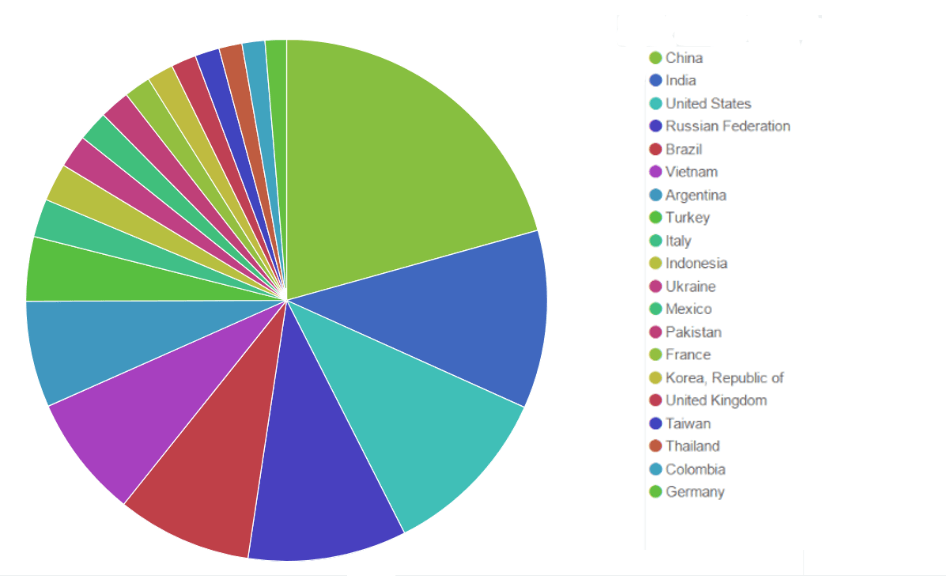
Before this case, the distribution of blacklisted IPs (in the whole BitNinja database) looked like this:
The TOP five attacking countries were:
- China
- India
- United States
- Russian Federation
- Brazil
But now, the hierarchy has changed:
The TOP 5 attacking countries during this incident look like this:
- India
- Brazil
- United States
- Pakistan
- Philippines
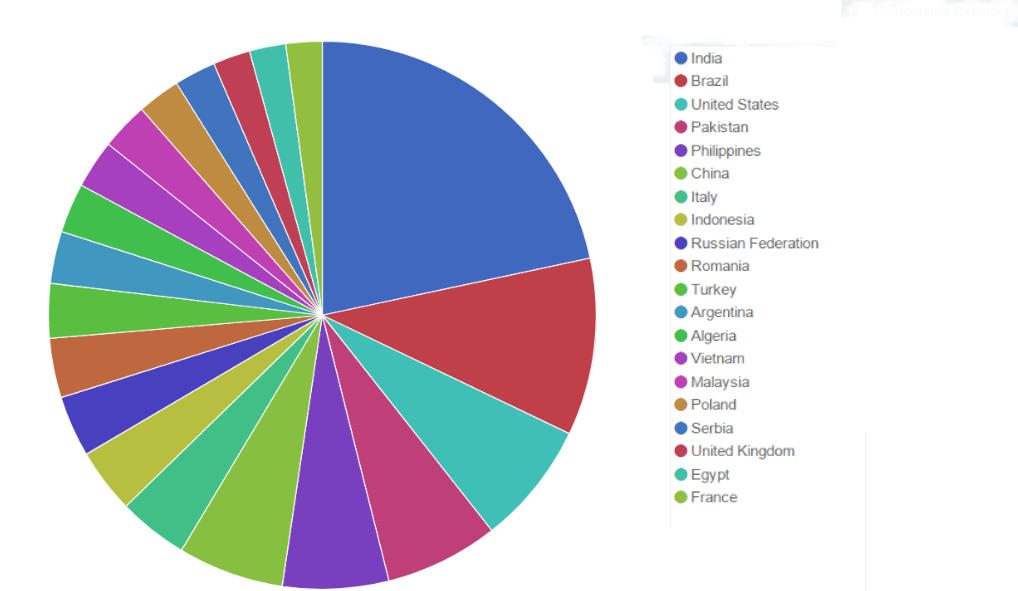
This huge attack has heavily reordered the hierarchy of the vicious countries.
That’s how some smart devices can change your and your server’s life. 🙂
Be protected, use BitNinja.
We provide a solution that let you manage who is able to enter to your server. 🙂
If you know a suspicious IP but you can't decide if it's good or bad one, put it on the BitNinja's greylist and lean back. With the help of collective intelligence the system can identify, the traffic was harmful or harmless.
 The scannings were in alphabetical order by the domain names, and we had one attack attempt for a server. So, a single server has never been attacked twice by the same IP. We don’t know the exact reason for it, maybe the attacker tried to avoid the blacklisting of his/her botnet.
The scannings were in alphabetical order by the domain names, and we had one attack attempt for a server. So, a single server has never been attacked twice by the same IP. We don’t know the exact reason for it, maybe the attacker tried to avoid the blacklisting of his/her botnet.
