The holidays are over already, and hackers didn’t sleep at all during that time. Yeah, a critical Joomla vulnerability is on board again.
To tell the truth, this 0-day remote command execution vulnerability is already 3-weeks old, but it can still cause headache for owners using versions from 1.5 to 3.4. It is a quite dangerous security hole, maybe the worst type of attack you may face, as hackers can easily manipulate your server this way. And even worse: the patch was released only after 2 days. It has been exploited in the wild.

As the BitNinja security system is continuously monitoring such issues, the BitNinja enabled servers were already protected against this exploit. The honeypot system still detects many more exploit attempts, but the ninja WAF* is intractable, keeping our users secured against this threat as well.
We know that the new year has just begun… But the tech ninjas are working hard on a new feature completing the WAF power. It will be able to detect 0-day attacks like this as quick as thought, helping BitNinja to protect within 1 hour against them. Hm, maybe we should call this 0-hour threat. 🙂
* You have already installed BitNinja on your server, but the ninja WAF is still inactive? Here is the manual how to activate the WAF
To avoid 0-day attacks next time, sign up for the 7-day BitNinja trial, and let it resolve such issues

By the way, the version 1.9.9 has been just released
*** CaptchaSMTP module is available ***
CaptchaSMTP module is used to identify false positives on the BitNinja greylist and allow human mail users to remove themselves from the greylist easily.
In other words if an IP is placed to the BitNinja greylist, and try to access your server through SMTP, the request will be forwarded to an alternative fake mail server (created by BitNinja) we log the commands sent by the remote server and create and incident out of them. At the same time we reply to the server with the following message:
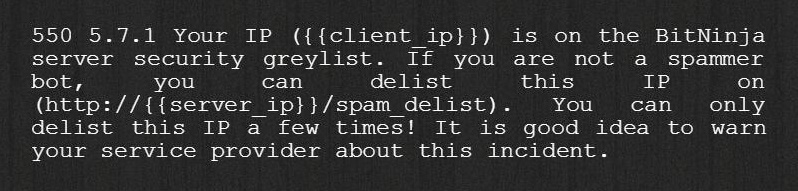
So if it was a false positive, the users can delist their IPs, but in case of automatic spam activity we log the incidents.

